Getting Started
To test beta versions of apps and App Clips using TestFlight, you’ll need to accept an email or public link invitation from the developer and have a device that you can use to test.
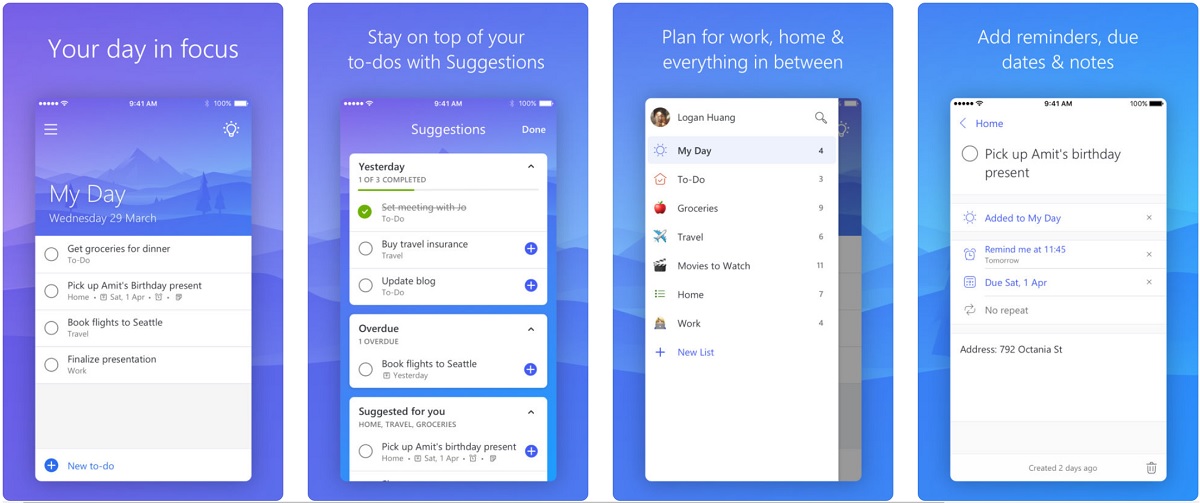
IOS widgets and Microsoft To Do People on iOS 14 who use To Do on version 2.37 and above can create widgets for To Do. You can view existing tasks in the widget, add new tasks to your lists, and open and access any list. It’s not currently possible to mark tasks as complete in a widget.
- If the app is an iOS app that includes an Apple Watch app, install the iOS app first, then from the App Details page under the Information section, you will see a Watch section. If the Apple Watch app is available and compatible with your watch, you’ll see a button to install it.
- Microsoft To Do iOS 14 widgets are now available ashokobhan. Microsoft To Do Blog. Focus on what matters with AI in To Do Shashank Gandhi.
Members of the developer’s team can be given access to all builds of the app.
All other invited testers can access builds that the developer makes available to them. A developer can invite you to test with an email or a public link.
Required platforms
- iOS apps: iPhone, iPad, or iPod touch running iOS 8 or later. App Clips require iOS 14 or later. iMessage apps and sticker packs require iOS 10 or later.
- tvOS apps: Apple TV running tvOS 9 or later.
- watchOS apps: Apple Watch running watchOS 2 or later.
TestFlight is not available for Mac apps.
Available Languages
TestFlight for both iOS and tvOS is available in Arabic, Catalan, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English (Australia), English (U.K.), English (U.S.), Finnish, French, French (Canada), German, Greek, Hebrew, Hindi, Hungarian, Indonesian, Italian, Japanese, Korean, Malaysian, Norwegian, Polish, Portuguese (Brazil), Portuguese (Portugal), Romanian, Russian, Slovak, Spanish, Spanish (Latin America), Swedish, Thai, Turkish, Ukrainian, and Vietnamese.
Installing and Testing Beta Apps
Each build is available to test for up to 90 days, starting from the day the developer uploads their build. You can see how many days you have left for testing under the app name in TestFlight. TestFlight will notify you each time a new build is available and will include instructions on what you need to test. Alternatively, with TestFlight 3 or later, you can turn on automatic updates to have the latest beta builds install automatically.
When the testing period is over, you'll no longer be able to open the beta build. To install the App Store version of the app, download or purchase the app from the App Store. In-app purchases are free only during beta testing, and any in-app purchases made during testing will not carry over to App Store versions.
Installation
To get started, install TestFlight on the device you’ll use for testing. Then, accept your email invitation or follow the public link invitation to install the beta app. You can install the beta app on up to 30 devices.
Installing a Beta iOS App via Email or Public Link Invitation
- Install TestFlight on the iOS device that you’ll use for testing.
- Open your invitation email or tap on the public link on your iOS device.
- Tap View in TestFlight or Start Testing; or tap Install or Update for the app you want to test.
Installing a Beta tvOS App via Email Invitation
- Install TestFlight on Apple TV.
- Open your invitation email on a mobile device or computer.
- Click or tap Start Testing. You'll be taken to a web page with a redemption code.
- Open TestFlight on Apple TV.
- Go to Redeem and enter the redemption code.
Installing a Beta tvOS App via Public Link Invitation
- Install TestFlight on an iOS device and Apple TV where you can sign in to the same App Store account.
- Tap the public link on your iOS device.
- Tap Accept for the app you want to test.
- Open TestFlight on Apple TV. You must be signed in to the same App Store account you used on your iOS device.
- Install the app you want to test.
Installing a Beta watchOS App via Email or Public Link Invitation
- Install TestFlight on the iOS device that you’ll use for testing.
- Open your invitation email or tap on the public link on your iOS device.
- Tap View in TestFlight or Start Testing.
- If you're testing an app that’s for Apple Watch only, tap Install or Update from the Apps list.
- If the app is an iOS app that includes an Apple Watch app, install the iOS app first, then from the App Details page under the Information section, you will see a Watch section. If the Apple Watch app is available and compatible with your watch, you’ll see a button to install it.
Testing
Testing iMessage Apps (iOS 10 or later)
- Install TestFlight on the iOS device that you’ll use for testing.
- Open your invitation email or tap on the public link on your iOS device.
- Tap View in TestFlight or Start Testing; or tap Install or Update for the app you want to test.
- If you’re testing an iOS app that includes an iMessage app, launch the beta app from the home screen as you would with any app.
- If you’re testing an app that’s for iMessage only or a sticker pack, you can launch it from inside Messages.
Testing Beta App Clips (iOS 14 or later)
After accepting your email or public link invitation to test the app, you’ll see the option to test the App Clip in TestFlight. You can install either the app or the App Clip on your device (but not both at once), and can replace one with the other at any time. If the app is installed on your device, testing the App Clip will replace the app and some app data may be lost. You can reinstall the app by tapping Install on the app’s page in TestFlight.
- Install TestFlight on the iOS device that you’ll use for testing.
- Open your invitation email or tap on the public link on your iOS device.
- Tap View in TestFlight or Start Testing; or tap Install or Update for the app you want to test.
- Go to the app’s page in TestFlight.
- In the App Clips section, tap TEST next to the beta App Clip you want to test.
Managing Automatic Updates
After installing TestFlight 3 or later, you’ll be prompted to turn on automatic updates. This allows the latest available beta builds to install automatically. TestFlight will notify you each time a new build is installed on your device. Automatic updates can be turned off at any time.
Change automatic update settings for all of the beta apps you’re testing using TestFlight:
TestFlight for iOS
- Open TestFlight and tap Settings in the upper-right corner.
- Tap Automatic Updates.
- Tap On or Off.
TestFlight for tvOS
- Open TestFlight and click the Settings tab at the top.
- Under GENERAL INFORMATION, turn Automatic Updates On or Off.
Change automatic update settings for individual beta apps you’re testing using TestFlight:
TestFlight for iOS
- Open TestFlight and go to the app’s page.
- Under App Information, turn Automatic Updates On or Off.
TestFlight for tvOS
- Open TestFlight and go to the app’s page.
- Under the app icon, click the More button.
- Click Turn On Automatic Updates or Turn Off Automatic Updates.
Testing Previous Builds
When viewing an app in TestFlight, you'll see the latest available build by default. You can still test all other builds that are available to you.
- Go to the app’s page in TestFlight.
- Tap on Previous Builds.
- Tap and install the build you want to test. The one you select will replace what’s currently installed.
If you already have the App Store version of the app installed on your device, the beta version of the app will replace it. After you download the beta app, you’ll see an orange dot next to its name that identifies it as a beta.
When you accept a TestFlight invitation through a public link, your name and email address are not visible to the developer. However, they’ll be able to see your number of sessions and crashes, the day you installed their app, and the latest installed version.
Giving Feedback
While testing a beta version of an app or App Clip, you can send the developer feedback about issues you experience or make suggestions for improvements based on the “What to Test” content. Feedback you submit through TestFlight is also provided to Apple as part of the TestFlight service.
iOS Apps
If your device is running iOS 13 or later, you can send feedback through the TestFlight app or directly from the beta app or beta App Clip by taking a screenshot, and you can report a crash after it occurs. If you were invited to test an app with a public link, you can choose not to provide your email address or other personal information to the developer. Apple will also receive all feedback you submit and will be able to tie it to your Apple ID.
Sending Feedback through the TestFlight App (iOS 13 or later)
- Open the TestFlight app on your device.
- From the Apps list, tap the app.
- Tap Send Beta Feedback.
- In the share dialog, tap Include Screenshot to choose a screenshot. If you don’t want to send an attachment, tap Don't Include Screenshot.
- Add your comments (up to 2,000 characters), and optionally enter your email address if you were invited with a public link.
- Tap Submit.
Sending Feedback through the Beta App (iOS 13 or later)
When you take a screenshot while testing a beta app or beta App Clip, you can send the screenshot with feedback directly to the developer without leaving the app or App Clip Experience. Developers can opt out of receiving this type of feedback, so this option is only available if the developer has it enabled.
- Take a screenshot on your device. For details on how to take screenshots, see Take a screenshot on your iPhone, Take a screenshot on your iPad, and Take a screenshot on your iPod touch.
- A thumbnail of your screenshot appears in the lower-left corner of your device. Tap the thumbnail and, if needed, add drawings and text with Markup. Then tap the Done button.
- Tap the Share Beta Feedback.
- Optionally, you can add comments (up to 2,000 characters), and your email address if you were invited with a public link.
- Tap Submit.
Sending Crash Information (iOS 13 or later)
If you experience a crash while testing a beta app or beta App Clip, you’ll receive an alert asking if you want to send crash details to the developer through TestFlight. Developers can opt out of receiving this type of feedback, so this option is only available if the developer has it enabled.
When the crash alert displays, tap Share, add any additional comments, and tap Submit.
Sending Feedback through the TestFlight App (iOS 12.4 or earlier)
If your device is running iOS 12.4 or earlier, tap Send Beta Feedback to compose an email to the developer. The feedback email contains detailed information about the beta app and about your iOS device. You can also provide additional information, such as necessary screenshots and steps required to reproduce any issues. Your email address will be visible to the developer when you send email feedback through the TestFlight app even if you were invited through a public link.
Contacting the Developer
If you need to contact the developer while you’re testing their beta app for reasons other than feedback, you can view their email address. In TestFlight, go to the app’s page, go to the Information section, and tap App Details to view the developer’s email address.
tvOS Apps
To provide feedback on a tvOS app, open TestFlight, go to app’s page, go to the Information section to view the developer's email address, and send them an email. Provide as much information as you can, including screenshots and steps required to reproduce any issues you encountered. Please note that your email address will be visible to the developer when you send email feedback through TestFlight.
Opting Out from Testing
If you do not accept your email invitation, the beta app will not be installed and you will not be listed as a tester, and Apple will not take any action with respect to your email address. Additionally, you can unsubscribe using the link at the bottom of the invitation email to notify the developer that you’d like to be removed from their list. If you accepted the invitation and no longer wish to test the app, you can delete yourself as a tester in the app’s Information page in TestFlight by tapping Stop Testing.
Your Privacy and Data
When you test beta apps and beta App Clips with TestFlight, Apple will collect and send crash logs, your personal information such as name and email address, usage information, and any feedback you submit to the developer. Information that is emailed to the developer directly is not shared with Apple. The developer is permitted to use this information only to improve their App and is not permitted to share it with a third party. Apple may use this information to improve the TestFlight app.
Apple retains TestFlight data for one year. To view and manage your data with Apple, including your data that is sent to Apple through TestFlight, visit Data and Privacy. For more information about how the developer handles your data, consult their privacy policy. To request access to or deletion of your TestFlight data, you should contact the developer directly.
Information Shared by Using TestFlight
The following data is collected by Apple and shared with the developer when you use TestFlight. If you accepted an invitation through a public link only, your email address and name are not visible to the developer.
| Data | Description |
|---|---|
| Email Address | The email address with which you were invited to test the app with. This may or may not be the same as the Apple ID associated with your device. If you were invited with a public link, your email address is not shared with the developer. |
| Name | Your first and last name as entered by the developer when they invited you to test the app using your email address. If you were invited with a public link, your name is not shared with the developer. |
| Invitation Type | Whether you were invited by email or through a public link. |
| Status | The status of your invitation: Invited, Accepted, or Installed. This status is refreshed when you accept or install a beta build. |
| Installs | The number of times you've installed a beta build. |
| Sessions | The number of times you've used a beta build. |
| Crashes | The number of crashes per beta build. |
Data Shared When Sending Feedback (iOS only)
When you send feedback through TestFlight or send crashes or screenshots from the beta app, the following additional information is shared. If your device runs iOS 12.4 or earlier, this information is only shared with the developer. If your device runs iOS 13 or later, this information is collected by Apple and shared with developers. Apple retains the data for one year.
| Data | Description | When this data is included |
|---|---|---|
| App Name | The name of the app you are testing. | Included in all feedback |
| App Version | The most recent version and build that you have access to. This is the number that displays under the app name in the list of apps in TestFlight. | Included in all feedback |
| Installed App Version | The version and build you have installed on your device. | Included in all feedback |
| Device | The model of your device. | Included in all feedback |
| iOS Version | The version of iOS your device is running. | Included in all feedback |
| Language | Your device language. | Included in all feedback |
| Carrier | Your wireless service provider. | Included in all feedback |
| Time Zone | The time zone your device is set to. | Included in all feedback |
| Architecture | The type of Central Processing Unit (CPU) for your device. | Included in all feedback |
| Connection Type | Whether you were connected to Wi-Fi, cellular, or not connected at the time that the feedback was sent and your network type. | Included in all feedback |
| Paired Apple Watch | The model and watchOS version of the paired Apple Watch, if applicable. | Included in all feedback |
| Screenshots | The screenshots you shared when providing feedback. | Only on devices running iOS 13 or later |
| Comments | The comments you shared when providing feedback. | Only on devices running iOS 13 or later |
| App Uptime | The length of time the app was open and running at the time the feedback was sent. | Only on devices running iOS 13 or later |
| Disk Free | The amount of disk space you had available when you sent feedback. | Only on devices running iOS 13 or later |
| Battery | Your battery level at the time the feedback was sent. | Only on devices running iOS 13 or later |
| Screen Resolution | The screen resolution of your device. | Only on devices running iOS 13 or later |
| Crash Logs | Symbolicated crash logs. This includes information about how long the app was running before it crashed. | Only on devices running iOS 13 or later |
Office for iOS and Android delivers several key benefits including:
- Combining Word, Excel, and PowerPoint in a way that simplifies the experience with fewer apps to download or switch between. It requires far less phone storage than installing individual apps while maintaining virtually all the capabilities of the existing mobile apps people already know and use.
- Integrating Office Lens technology to unlock the power of the camera with capabilities like converting images into editable Word and Excel documents, scanning PDFs, and capturing whiteboards with automatic digital enhancements to make the content easier to read.
- Adding new functionality for common tasks people often encounter when working on a phone—things like making quick notes, signing PDFs, scanning QR codes, and transferring files between devices.
The richest and broadest protection capabilities for Microsoft 365 data are available when you subscribe to the Enterprise Mobility + Security suite, which includes Microsoft Intune and Azure Active Directory Premium features, such as conditional access. At a minimum, you will want to deploy a conditional access policy that allows connectivity to Office for iOS and Android from mobile devices and an Intune app protection policy that ensures the collaboration experience is protected.
Apply Conditional Access
Organizations can use use Azure AD Conditional Access policies to ensure that users can only access work or school content using Office for iOS and Android. To do this, you will need a conditional access policy that targets all potential users. Details on creating this policy can be found in Require app protection policy for cloud app access with Conditional Access.
Follow 'Step 1: Configure an Azure AD Conditional Access policy for Office 365' in Scenario 1: Office 365 apps require approved apps with app protection policies, which allows Office for iOS and Android, but blocks third-party OAuth capable mobile device clients from connecting to Office 365 endpoints.
Note
This policy ensures mobile users can access all Office endpoints using the applicable apps.
Create Intune app protection policies
App Protection Policies (APP) define which apps are allowed and the actions they can take with your organization's data. The choices available in APP enable organizations to tailor the protection to their specific needs. For some, it may not be obvious which policy settings are required to implement a complete scenario. To help organizations prioritize mobile client endpoint hardening, Microsoft has introduced taxonomy for its APP data protection framework for iOS and Android mobile app management.
The APP data protection framework is organized into three distinct configuration levels, with each level building off the previous level:
- Enterprise basic data protection (Level 1) ensures that apps are protected with a PIN and encrypted and performs selective wipe operations. For Android devices, this level validates Android device attestation. This is an entry level configuration that provides similar data protection control in Exchange Online mailbox policies and introduces IT and the user population to APP.
- Enterprise enhanced data protection (Level 2) introduces APP data leakage prevention mechanisms and minimum OS requirements. This is the configuration that is applicable to most mobile users accessing work or school data.
- Enterprise high data protection (Level 3) introduces advanced data protection mechanisms, enhanced PIN configuration, and APP Mobile Threat Defense. This configuration is desirable for users that are accessing high risk data.
To see the specific recommendations for each configuration level and the minimum apps that must be protected, review Data protection framework using app protection policies.
Regardless of whether the device is enrolled in an unified endpoint management (UEM) solution, an Intune app protection policy needs to be created for both iOS and Android apps, using the steps in How to create and assign app protection policies. These policies, at a minimum, must meet the following conditions:
They include all Microsoft 365 mobile applications, such as Edge, Outlook, OneDrive, Office, or Teams, as this ensures that users can access and manipulate work or school data within any Microsoft app in a secure fashion.
They are assigned to all users. This ensures that all users are protected, regardless of whether they use Office for iOS or Android.
Determine which framework level meets your requirements. Most organizations should implement the settings defined in Enterprise enhanced data protection (Level 2) as that enables data protection and access requirements controls.
For more information on the available settings, see Android app protection policy settings and iOS app protection policy settings.
Important
To apply Intune app protection policies against apps on Android devices that are not enrolled in Intune, the user must also install the Intune Company Portal. For more information, see What to expect when your Android app is managed by app protection policies.
Utilize app configuration
Office for iOS and Android supports app settings that allow unified endpoint management, like Microsoft Endpoint Manager, administrators to customize the behavior of the app.
App configuration can be delivered either through the mobile device management (MDM) OS channel on enrolled devices (Managed App Configuration channel for iOS or the Android in the Enterprise channel for Android) or through the Intune App Protection Policy (APP) channel. Office for iOS and Android supports the following configuration scenarios:
- Only allow work or school accounts
- General app configuration
- Data protection settings
Microsoft To-do Ios Download
Important
For configuration scenarios that require device enrollment on Android, the devices must be enrolled in Android Enterprise and Office for Android must be deployed via the Managed Google Play store. For more information, see Set up enrollment of Android Enterprise personally-owned work profile devices and Add app configuration policies for managed Android Enterprise devices.
Each configuration scenario highlights its specific requirements. For example, whether the configuration scenario requires device enrollment, and thus works with any UEM provider, or requires Intune App Protection Policies.
Important
App configuration keys are case sensitive. Use the proper casing to ensure the configuration takes affect.
Note
With Microsoft Endpoint Manager, app configuration delivered through the MDM OS channel is referred to as a Managed Devices App Configuration Policy (ACP); app configuration delivered through the App Protection Policy channel is referred to as a Managed Apps App Configuration Policy.
Only allow work or school accounts
Respecting the data security and compliance policies of our largest and highly regulated customers is a key pillar to the Microsoft 365 value. Some companies have a requirement to capture all communications information within their corporate environment, as well as, ensure the devices are only used for corporate communications. To support these requirements, Office for Android on enrolled devices can be configured to only allow a single corporate account to be provisioned within the app.
You can learn more about configuring the org allowed accounts mode setting here:
This configuration scenario only works with enrolled devices. However, any UEM provider is supported. If you are not using Microsoft Endpoint Manager, you need to consult with your UEM documentation on how to deploy these configuration keys.
Note
Microsoft To Do Ios Widget
At this time, only Office for Android supports org allowed accounts mode.
General app configuration scenarios
Office for iOS and Android offers administrators the ability to customize the default configuration for several in-app settings. This capability is offered for both enrolled devices via any UEM provider and for devices that are not enrolled when Office for iOS and Android has an Intune App Protection Policy applied.
Note
If an App Protection Policy is targeted to the users, the recommendation is to deploy the general app configuration settings in a Managed Apps enrollment model. This ensures the App Configuration Policy is deployed to both enrolled devices and unenrolled devices.
Office supports the following settings for configuration:
- Manage the creation of Sticky Notes
Manage the creation of Sticky Notes
By default, Office for iOS and Android enables users to create Sticky Notes. For users with Exchange Online mailboxes, the notes are synchronized into the user's mailbox. For users with on-premises mailboxes, these notes are only stored on the local device.
| Key | Value |
|---|---|
| com.microsoft.office.NotesCreationEnabled | true (default) enables Sticky Notes creation for the work or school account false disables Sticky Notes creation for the work or school account |
Data protection app configuration scenarios
Office for iOS and Android supports app configuration policies for the following data protection settings when the app is managed by Microsoft Endpoint Manager with an Intune App Protection Policy applied to the work or school account that is signed into the app and the policy settings are delivered only through a managed apps App Configuration Policy:
- Manage file transfers via Transfer Files action
- Manage file transfers via Share Nearby action
These settings can be deployed to the app regardless of device enrollment status.
Manage file transfers
By default, Office for iOS and Android enables users to share content using a variety of mechanisms:
Microsoft To-do Ios Free
- If the file is hosted in OneDrive or SharePoint, users can initiate a share request directly within the file.
- Users can transfer files to desktop systems using the Transfer Files action.
- Users can share files to nearby mobile devices using the Share Nearby action.
The Transfer Files and Share Nearby actions only work with media, local files, and files that are not protected by an App Protection Policy.
| Key | Value |
|---|---|
| com.microsoft.office.ShareNearby.IsAllowed.IntuneMAMOnly | true (default) enables the Share Nearby feature for the work or school account false disables the Share Nearby feature for the work or school account |
| com.microsoft.office.TransferFiles.IsAllowed.IntuneMAMOnly | true (default) enables the Transfer Files feature for the work or school account false disables the Transfer Files feature for the work or school account |
Deploy app configuration scenarios with Microsoft Endpoint Manager
If you are using Microsoft Endpoint Manager as your mobile app management provider, see Add app configuration policies for managed apps without device enrollment on how to create a managed apps app configuration policy for the data protection app configuration scenarios. After the configuration is created, you can assign the policy to groups of users.
All Microsoft Apps For Ios
Next steps
